Cybersecurity requirements for Financial Services companies
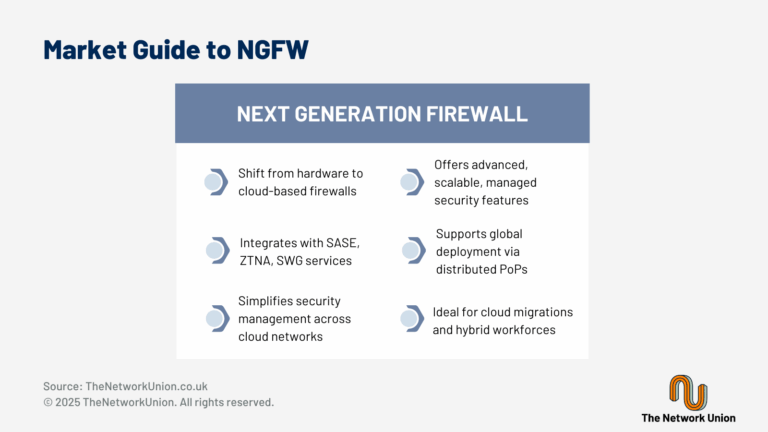
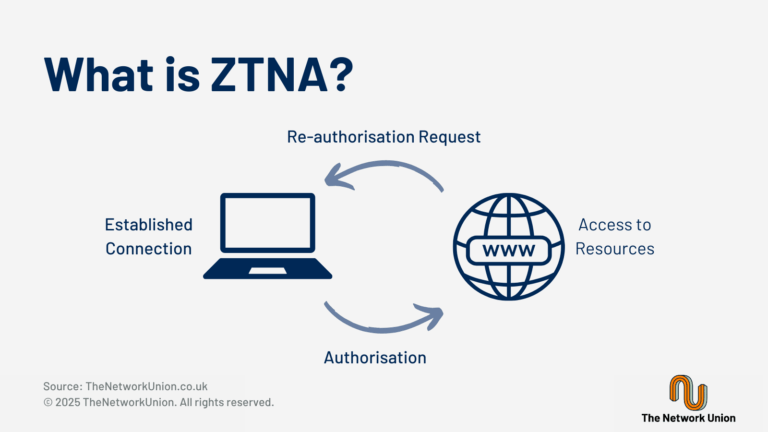
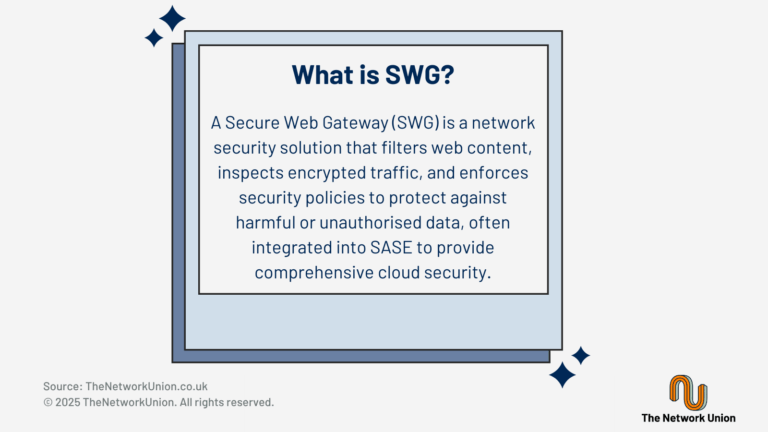
Financial Services face threats such as ransomware, data breaches and vulnerabilities from remote workforces. Solutions include access management, endpoint security, SD-WAN, FWaaS and compliance tools. Cyberattacks are on the rise, and the costs and impacts of ransomware, data breaches, and other cyberattack campaigns continue to grow. The combination of growing cybersecurity risk and expanding regulatory […]
Cybersecurity requirements for Financial Services companies Read More