IT Buyer’s Guide: Fortinet SD-WAN & SASE Network Security
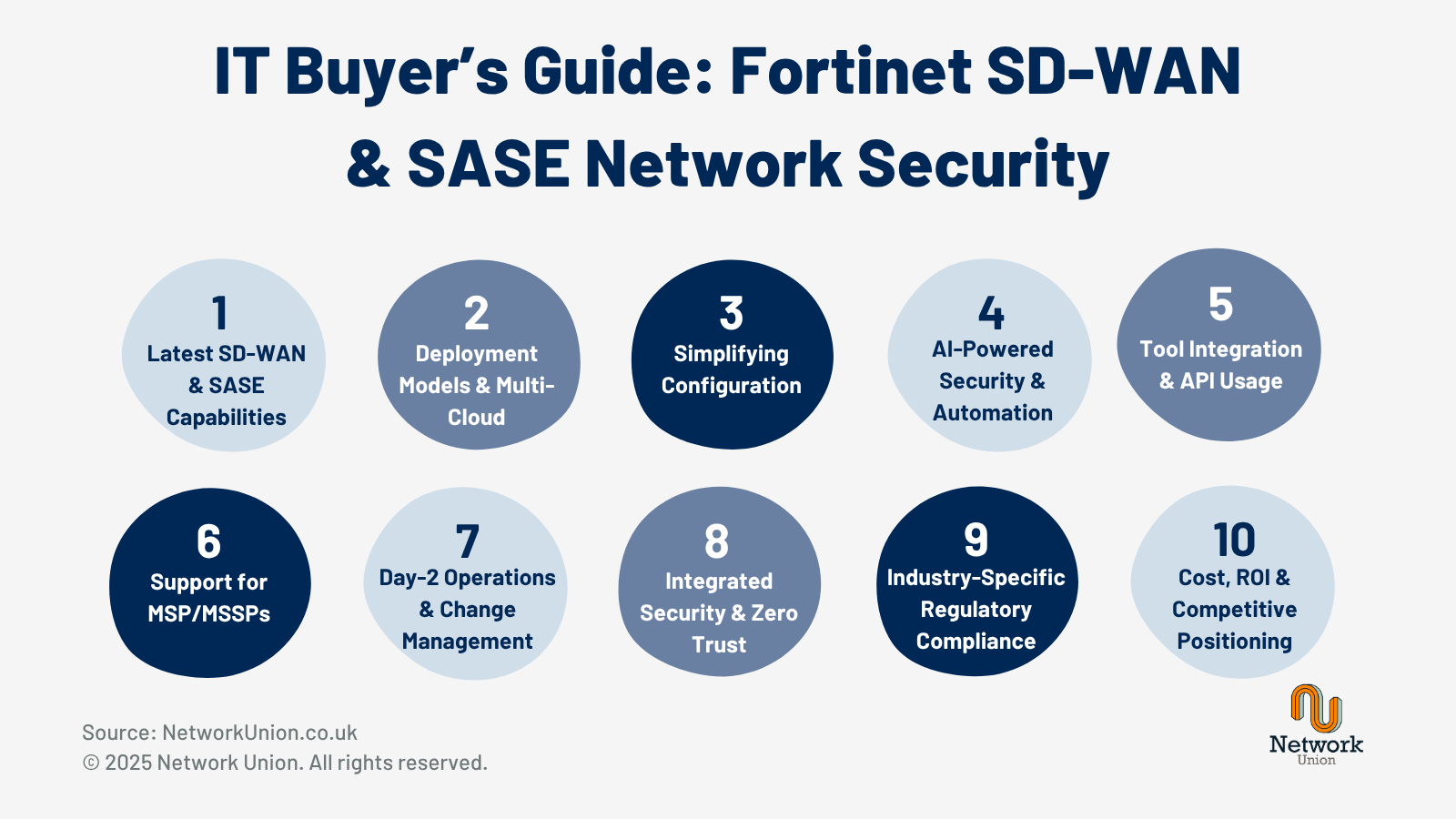
This buyer's guide provides IT decision-makers with an evaluation of Fortinet's SASE and SD-WAN offerings, focusing on practical deployment considerations, operational requirements and cost implications for buyers looking to shortlist Fortinet SD-WAN alongside alternative vendors.
Latest Capabilities and Roadmap (Fortinet Secure SD-WAN & SASE)
Fortinet's latest insights in SD-WAN and SASE developments focus primarily on cloud-native architectures, AI-powered security and advanced analytics.
These cloud improvements include cloud application acceleration, Microsoft 365 integrations and expanded Software-as-a-Service (SaaS) visibility with better branch-to-cloud connectivity optimisation.
To further improve their platform, the FortiGuard AI-powered ecosystem leverages predictive analytics for network performance and automated threat response. These features allow Fortinet's Security Fabric to use analytics for threat intelligence, automated policy recommendations, proactive network optimisation, predictive bandwidth allocation, intelligent application routing and automated failover to complete a full-featured AI-portfolio - providing a wide range of automation services, meeting efficiency requirements and offering security solutions to support the demands of modern security-postures.
Deployment Models and Multi-Cloud Integration
Hardware-based options use FortiGate next generation firewalls (NGFWs), ranging from branch devices to high-performance data centre platforms. These next generation firewall appliances consolidate multiple security services and networking functions into a single unit, delivering top-rated security at the network edge.
Virtual appliances, such as FortiGate VM, allow deployment across leading cloud providers such as AWS and Azure. These cloud-native options make it easier to deploy scalable, policy-consistent infrastructure aligned with operational expenditure (OpEx) models.
Multi-cloud environments benefit from FortiManager, which supports centralised security posture control and consistent policy enforcement across hybrid workforce and multi-cloud use cases. This allows for end to end security without introducing unnecessary network complexity, even when dealing with distributed remote users or migrating cloud applications.
For businesses considering Fortinet’s hybrid workforce deployment model, this might involve FortiGate appliances at branch locations connecting to FortiGate VM instances in Amazon Web Services (AWS) and Azure cloud environments. These would then all be managed and controlled via FortiManager, ensuring consistent security policies across all locations, whilst SD-WAN capabilities optimise application performance by selecting appropriate connectivity paths based on real-time conditions.
Once deployed, the ease of managing and orchestrating Fortinet's infrastructure becomes a key factor in long-term operational success.
Ease of Configuration and Orchestration
Fortinet Secure SD-WAN’s web-based management interface provides access to configuration and monitoring capabilities, with real-time monitoring, simplified dashboards and visibility into performance, system health and security events. Customisable reporting capabilities enable organisations to generate compliance reports and performance metrics aligned with business requirements, whilst integration with existing monitoring systems ensures that network information remains available through already established operational processes.
Like its competitors, Fortinet emphasises centralised management and automated deployment processes to reduce operational overhead, simplifying operations.
FortiManager provides unified policy management across distributed deployments. The platform enables administrators to define policies centrally and deploy them consistently across multiple locations and form factors. This includes security policies, routing configurations, and application optimisation settings. Configuration templates enable standardised deployments across similar locations, reducing manual configuration requirements. However, whilst these templates help with speeding up deployment and configuration, users report that manual changes to wizard-generated templates can often be overwritten when running the wizard again, leading to potential loss of custom configurations. This can make ongoing management cumbersome compared to some competitors that offer configuration tools without this weakness.
Rapid provisioning capabilities extend the platform to enable rapid provisioning and remote device deployment without on-site technical expertise. New devices are configured automatically upon initial connection, downloading appropriate configurations based on location-specific requirements. This process includes security certificates, policy configurations and connectivity settings.
How Fortiguard AI Powered Security and Networking Eases Configuration
AI-powered network and security capabilities automatically adjust routing decisions based on application performance metrics and business policies, whilst also enabling AI-powered threat intelligence to stay ahead of potential threats without requiring manual intervention for either task and therefore alleviating much of the manual day-to-day work.
However, for businesses concerned about leaving all of this up to automation, rollback capabilities ensure that problematic changes can be quickly reversed if issues arise. On top of this, remote troubleshooting capabilities enable centralised technical teams to resolve issues without requiring on-site visits.
Integration of External Tools with Fortigate
RESTful APIs enable integration with existing operational tools, professional services and custom automation scripts. This allows organisations to incorporate Fortinet management into broader infrastructure automation initiatives and integrate with configuration management platforms. Scripting capabilities support bulk configuration changes and automated response to network events, which is particularly valuable for large-scale deployments where manual management would be impractical.
The platform's extensive feature set can introduce complexity that may overwhelm organisations without sufficient technical expertise and therefore this complexity should be noted when shortlisting Fortinet.
Organisations typically report reduced deployment timeframes and lower operational overhead after implementing these automation capabilities. However, realising these benefits requires investment in training and process development to fully utilise the platform's capabilities.
Managed Services and MSP/MSSP Enablement
Beyond enterprise deployments, Fortinet Secure SD-WAN also supports service providers through multi-tenant management and automation features designed for Managed Service Providers (MSP) and Managed Security Service Providers (MSSP) environments.
One way this is achieved is through tenant isolation capabilities, which extends to reporting and monitoring capabilities, ensuring that client data remains segregated whilst enabling service providers to maintain operational oversight. In addition to that, role-based access controls enable client administrators to manage their specific environments without accessing other tenants' configurations.
For example, network and security operations centres benefit from unified visibility across multiple client environments. The Security Fabric supports multi-tenant control with granular control, role-based access and isolated data per client. Providers can integrate with billing systems, ticketing platforms, and offer security service edge capabilities through Fortinet’s Security Services, including malware protection, threat intelligence and policy enforcement, alongside automated alerting and escalation processes that can be customised for each client when leveraging shared operational resources. This approach is ideal for many MSPs as it enables service providers to deliver consistent service levels across differing client requirements.
Service providers can deliver managed SASE and SD-WAN services more readily through AI and automated capabilities, including security inspection, threat intelligence and policy enforcement services.
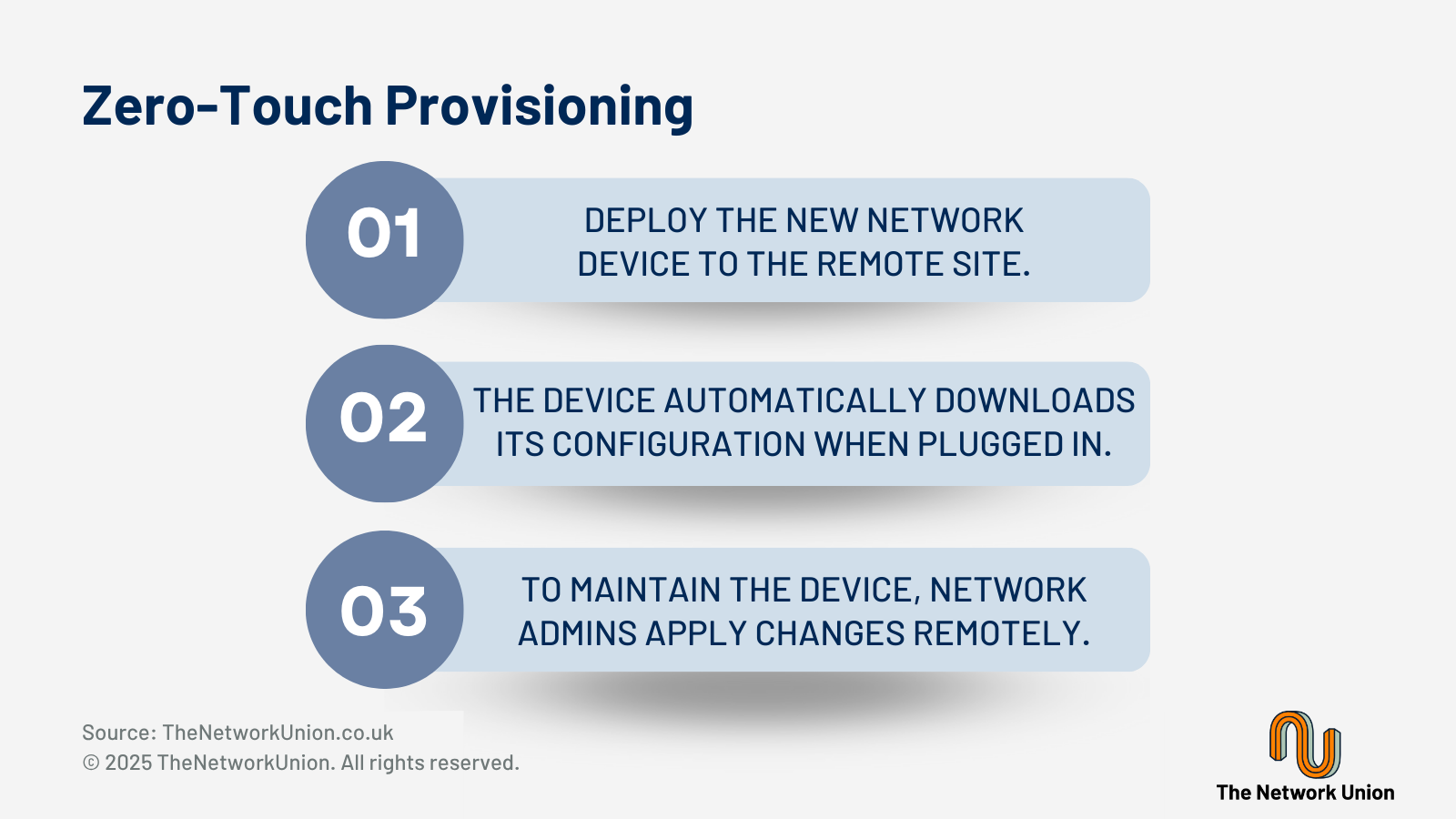
Day-2 Operations: Adds, Moves and Changes
Following deployment, the ability to efficiently manage ongoing changes, such as adds, moves and policy updates, is essential for operational agility. Due to their AI and security focus, Fortinet's approach emphasises automated processes and centralised management to minimise operational overhead associated with routine changes and consistency in policies between sites.
For new sites, automated deployment uses rapid provisioning based on predefined templates and location-specific requirements - ensuring consistency even at the newest of locations. To ensure everything has gone smoothly, Fortinet also implements validation processes so that new sites integrate properly with existing infrastructure and comply with organisational policies.
Policy changes benefit from automated approval processes and rollback capabilities that ensure changes align with organisational requirements and can be reversed if issues arise. Automated testing validates policy effectiveness and identifies potential conflicts before deployment.
For businesses utilising an OpEx model and wanting to only pay for used resources, cloud edge scaling leverages cloud resources through APIs and automated scaling processes to change resource allocations based on demands. Through dynamic capacity management, Fortinet SD-WAN adjusts resources based on demand patterns, ensuring consistent performance whilst optimising infrastructure costs based on actual utilisation. Modifications to cloud connectivity and services are managed through automated processes that minimise service disruption, again aligning with Fortinet's approach to use AI to reduce operational overhead.
This is achieved through machine learning algorithms, which identify patterns in network behaviour and proactively adjust configurations to prevent performance degradation and security incidents. These automated responses reduce the operational burden on technical teams whilst maintaining service quality, with organisations reporting that the automated change management processes significantly reduce the operational overhead associated with distributed infrastructure management.
Integrated Security Features and Zero Trust Networking in Fortinet Security Fabric and Fortigate NGFW
Fortinet stands out for its deep integration of security capabilities, particularly around zero trust and threat intelligence, therefore making Fortinet's Security Fabric a key differentiator within the market.
With Next Generation Firewall (NGFW) capabilities integrated into their SD-WAN appliances, Fortinet provide consistent security policies across distributed locations, which extends to application control, intrusion prevention, web filtering and threat protection at each network edge.
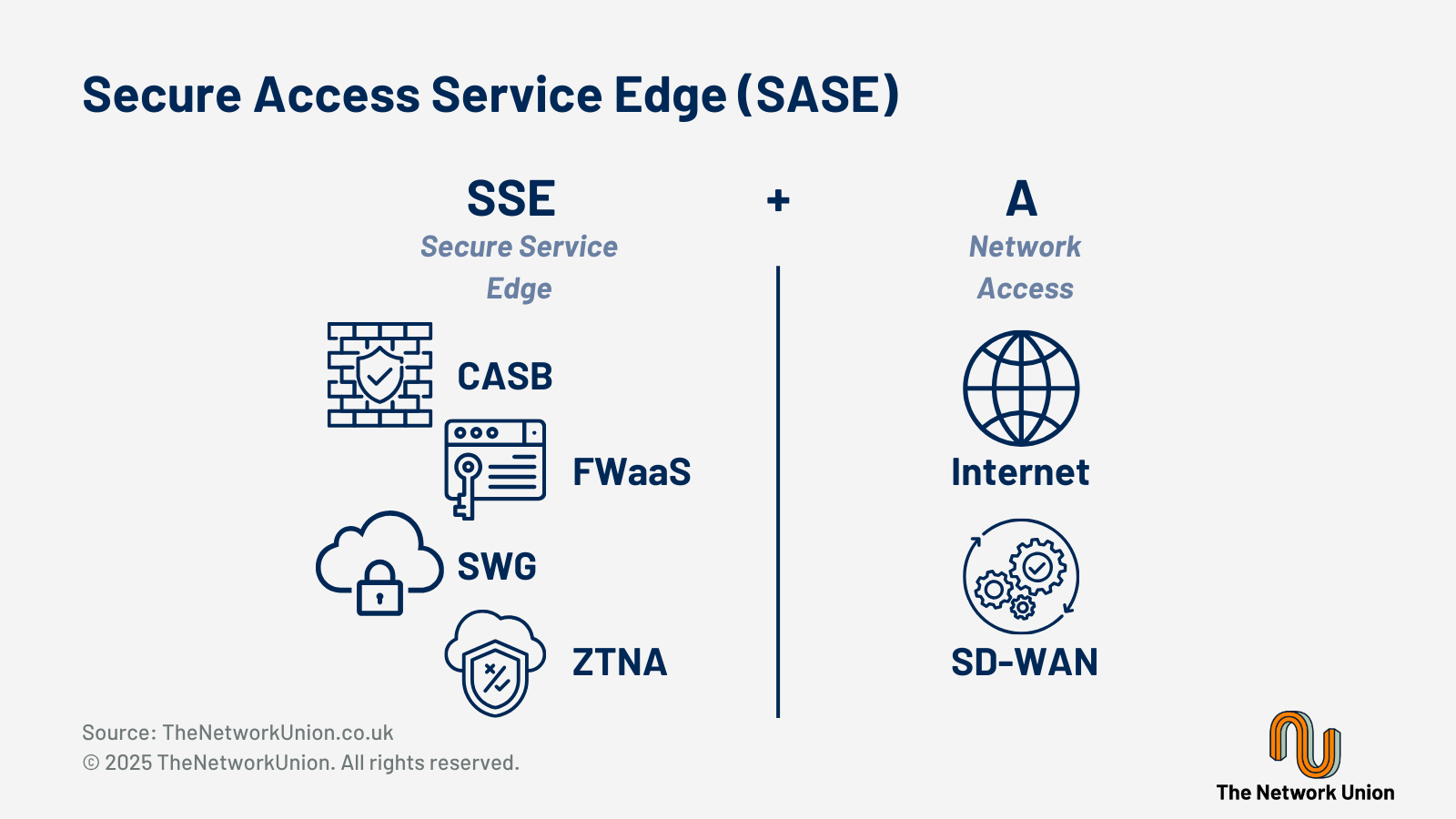
Following on from this, FortiSASE builds on Fortinet's SD-WAN and provides cloud-based security services including Secure Web Gateway, Cloud Access Security Broker and Zero Trust Network Access capabilities, with the integration between on-premises and cloud-delivered security services ensuring consistent protection across hybrid environments.
Identity-based access controls integrate with existing identity providers to enforce user and device authentication requirements. Policies can be defined based on user roles, device trust levels and application requirements rather than traditional network-based controls. Zero trust implementation extends beyond user access to include device verification and application-level policies that continuously validate access requirements, using micro-segmentation and continuous verification.
To go alongside their identity-based access controls, Fortinet provides real-time threat intelligence feeds that provide current information about emerging threats and attack patterns - ensuring that even new insider attack methods are detected as quickly as possible. This intelligence is automatically integrated into security policies and threat detection systems across the distributed infrastructure, with capabilities include sandboxing, machine learning-based anomaly detection and behavioural analysis that identify sophisticated attacks that traditional signature-based systems might miss.
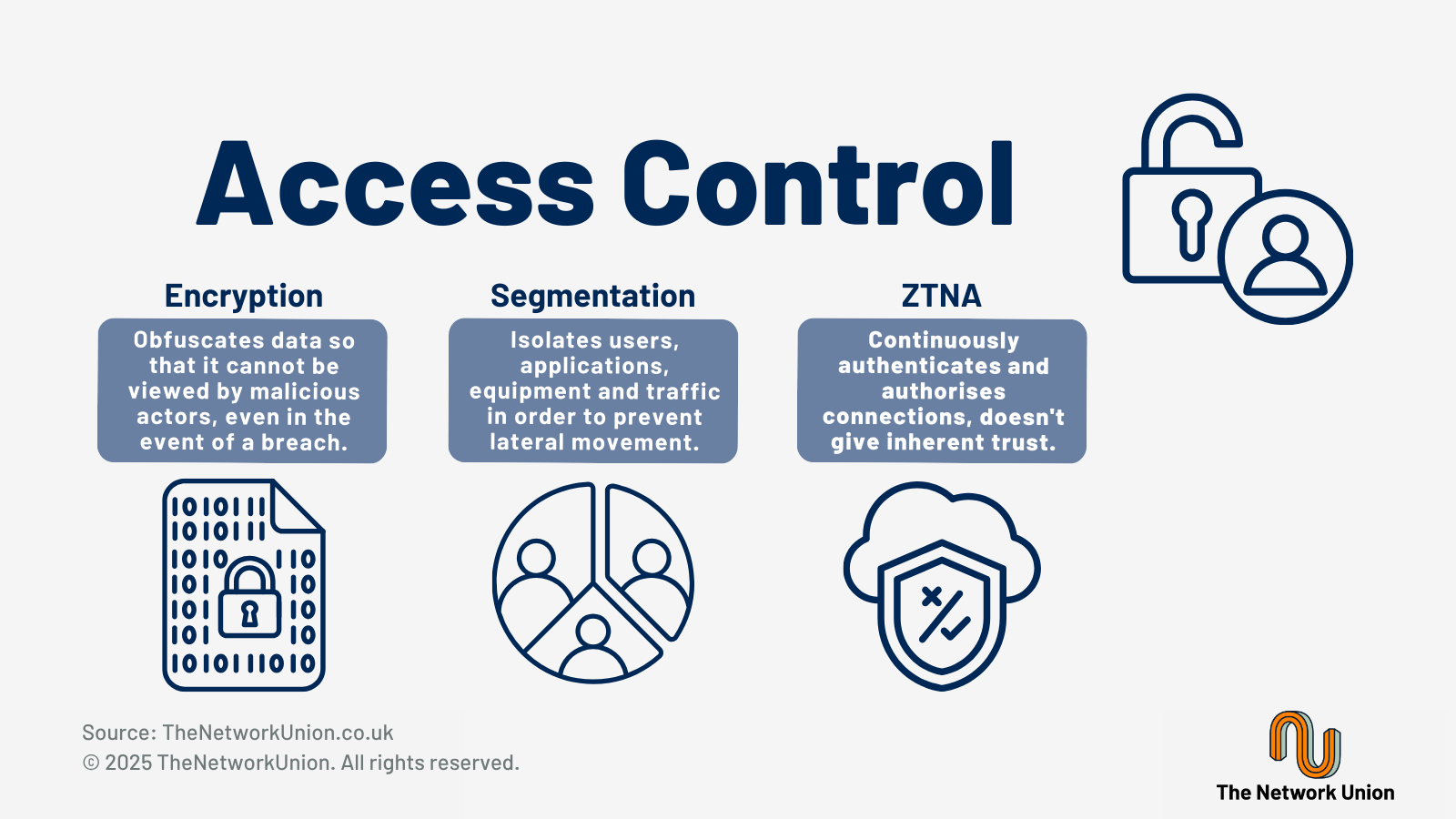
Finally, Fortinet offers integrations with third-party security tools to extend threat intelligence and incident information to existing security operations processes and tools.
Industry-Specific Capabilities and Use Cases
These security capabilities are further tailored to meet the unique demands of different industries, making Fortinet a shortlist-worthy choice across sectors, with unique requirements for SD-WAN and SASE implementations that Fortinetaddresses.
Healthcare
Fortinet's platform provides HIPAA-compliant configurations and healthcare-specific security policies that protect patient data whilst enabling efficient clinical workflows. Medical device connectivity is secured through network segmentation and device-specific policies that prevent unauthorised access whilst maintaining clinical functionality. Integration with healthcare identity systems ensures that access controls align with clinical roles and responsibilities. This often leads to reduced compliance audit findings, improved clinical application performance and better protection for patient data across distributed healthcare facilities.
Retail
Retail environments require reliable connectivity for point-of-sale systems and inventory management whilst protecting customer payment data. Fortinet provides PCI DSS-compliant configurations and retail-specific traffic prioritisation policies. Branch office standardisation reduces operational complexity across distributed retail locations, whilst integrations for retail-specific applications optimise transaction processing and inventory management systems.
Financial Services
Financial institutions require stringent security controls and regulatory compliance capabilities. Trading floor and financial application connectivity benefits from ultra-low latency optimisation and redundant connectivity options that ensure continuous operation during market hours. Alongside this, their compliance reporting capabilities provide detailed audit trails for regulatory requirements.
Manufacturing
Fortinet provides operational technology (OT) network segmentation and manufacturing-specific security policies. Industrial internet of things (IIoT) device connectivity is secured through device-specific policies and network isolation that prevents unauthorised access to essential manufacturing systems and reduced production downtime through reliable industrial connectivity.
Cost Analysis: Licensing Models, ROI, and Operational Overhead
Whilst physical capabilities are important, cost remains a central concern for many businesses. Fortinet’s pricing model and return on investment play a crucial role in vendor selection - with Fortinet utilising a combination of hardware costs and subscription-based licensing for security services and support.
It's worth noting that hardware appliances require initial capital expenditure with ongoing maintenance contracts for hardware support and software updates. However, FortiGate appliances provide competitive price-to-performance ratios compared to alternative vendors and multiple functions are integrated into single devices, potentially reducing overall hardware requirements compared to best-of-breed approaches.
If your business utilises an OpEx model, Fortinet's subscription licensing covers security services including threat intelligence, web filtering, application control and cloud-delivered SASE components, with licensing terms typically ranging from one to five years with discounts available for longer commitments - therefore it's worthwhile considering which of these subscriptions will be necessary for your use case when managing expenditure.
These aren't the only subscription-based costs though, with Fortinet's virtual and cloud deployments utilising subscription-based licensing that includes software usage rights and security services.
Cost Comparison with Other Vendors
Cisco solutions often require separate security appliances and licensing that can increase total costs compared to Fortinet’s slightly more integrated approach. However, Cisco may provide advantages in environments already leveraging existing Cisco infrastructure.
Whilst Palo Alto Networks is also well-known for security capabilities, they typically command premium pricing for security capabilities, therefore increasing overall solution costs compared to Fortinet.
ROI and Future Cost
Quantifiable benefits include reduced circuit costs through improved utilisation, decreased security incident costs through improved protection and enhanced productivity through better application performance.
Future cost considerations include hardware refresh cycles, expanding security service requirements and cloud migration impacts on licensing and operational costs.
Competitive Positioning and Comparison Against Other Networking and Security Specialists' SD-WAN solutions
Arguably the most important consideration though is how Fortinet's offering compares against other leading vendors in the SD-WAN and SASE market, including Cisco, Palo Alto Networks and VMware.
Cisco vs Fortinet
Cisco's approach emphasises intent-based networking and routing protocol support. The advantage lies in integrated security capabilities that eliminate the need for separate security appliances whilst providing consistent policy management.



Palo Alto Networks vs Fortinet
Palo Alto Networks focuses on security-centric approaches through Prisma SD-WAN and Prisma Access SASE services. However, their solution typically requires more components than Fortinet's integrated approach.
VMware VeloCloud vs Fortinet
VMware focuses primarily on SD-WAN orchestration and application optimisation with security provided through cloud services and partner integrations. In comparison, Fortinet provides more comprehensive integrated security capabilities than VMware's offering.

Fortinet's Key Advantages
Primary advantages include comprehensive security integration, unified management across networking and security functions and competitive total cost of ownership for integrated requirements. The Security Fabric architecture provides coordinated threat response capabilities across distributed environments. Hardware performance and integrated capabilities often provide better price-to-performance ratios compared to multi-vendor approaches.
Fortinet's Weaknesses
The platform's extensive feature set can introduce complexity that requires significant technical expertise to utilise effectively.
Frequently Asked Questions
What is Fortinet's Gartner Status?
Fortinet is a leader in the Gartner Magic Quadrant, recognised for their Fortinet Secure SD-WAN solution with end-to-end SASE capability. Fortinet's SD-WAN edge services are delivered by FortiGate physical and virtual appliances with their on-premises security software licenses delivered via FortiManager's Orchestrator. Fortinet supports approximately 31,000 global SD-WAN enterprise customers across various industries. Over the next 18 months, Fortinet's development efforts will focus on integrating digital experience monitoring (with SD-WAN for unified management), deploying an AI-based assistant, and enhancing internet and application performance to improve the customer experience.
What are the Pros & Cons of Fortinet SD-WAN?
Fortinet Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 04/11/2024 03:23 PM | hyelland | 04/11/2024 03:23 PM | ✓ Leadership Position: Fortinet is recognised as a Leader in Gartner's Magic Quadrant. | ❌ Customer Experience: Some feedback indicates a below-average customer experience, as per Gartner client Peer reviews. |
| 2 | hyelland | 04/11/2024 03:23 PM | hyelland | 04/11/2024 03:23 PM | ✓ Integrated Security: Offers a vast amount of SASE security experience. | ❌ Networking Capabilities: Concerns from large global clients about Fortinet's ability to handle complex enterprise networking requirements. |
| 3 | hyelland | 04/11/2024 03:23 PM | hyelland | 04/11/2024 03:23 PM | ✓ Strong Market Share and Sales Execution: Fortinet has significant market share via range channel partners. | ❌ Limited SSE Integrations: Fortinet's current limited integrations with third-party Secure Service Edge (SSE) vendors might restrict choices in deploying dual-vendor SASE architectures. |
| 4 | hyelland | 04/11/2024 03:23 PM | hyelland | 04/11/2024 03:23 PM | ✓ Expansive Global Reach: Approximately 31,000 enterprise customers worldwide. | |
| 5 | hyelland | 04/11/2024 03:23 PM | hyelland | 04/11/2024 03:23 PM | ✓ Future Investments: Focused on integrating digital experience monitoring with SD-WAN, an AI-based assistant, and improved internet and application performance. | |
| 6 | hyelland | 04/11/2024 03:23 PM | hyelland | 04/11/2024 03:23 PM | ✓ Cost Effective: Fortinet are viewed as a cost effective provider with good ROI. | |
| Pros | Cons |
What are the Pros & Cons of Fortinet SASE
Fortinet SASE Pros & Cons
| wdt_ID | wdt_created_by | wdt_created_at | wdt_last_edited_by | wdt_last_edited_at | Pros | Cons |
|---|---|---|---|---|---|---|
| 1 | hyelland | 23/10/2024 11:12 AM | hyelland | 23/10/2024 11:12 AM | ✓ Simplified Deployment: Easy and quick to deploy. | ❌ Limited Legacy Application Support: Limited support for legacy applications. |
| 2 | hyelland | 23/10/2024 11:12 AM | hyelland | 23/10/2024 11:12 AM | ✓ Advanced Security: Provides advanced security features. | ❌ Highly Secure Branch Office and Remote Users: Advanced security features may be challenging for branch offices and remote users. |
| Pros | Cons |
What industries do Fortinet deliver solutions for?
Fortinet offer solutions for the following industry verticals:
- Communications
- Federal Government
- Financial Services
- Healthcare
- Higher Education
- Hospitality
- K-12 School Districts
- Manufacturing
- Media and Entertainment
- Oil and Gas
- Pharmaceutical
- Power and Utilities
- Retail
- SCADA Control Systems
- State and Local Government
- Technology
- Transportation
What regulations do Fortinet comply with?
Fortinet offers compliance solutions for the following regulatory requirements:
- Children’s Internet Protection Act (CIPA)
- Family Educational Rights and Privacy Act (FERPA)
- General Data Protection Regulation (GDPR)
- Health Insurance Portability and Accountability Act (HIPAA)
- Payment Card Industry Data Security Standard (PCI-DSS)
- Privacy Amendment (Notifiable Data Breaches) Bill 2016
Fortinet Open Fabric Ecosystem Alliance Partners
Application Programming Interfaces (APIs):
- 1touch.io
- ABB
- Acalvio
- ADVA Optical Networking
- Advantech
- Aislelabs
- Alcide
- Algosec
- Altran
- Amdocs
- Ampere
- Anomali
- AppNeta
- AppViewX
- Aptilo Networks
- Area 1
- Arista Networks
- Arm
- Armis
- Array Networks
- Asavie
- Asimily
- ATAR Labs
- Attivo Networks
- AudioCodes Ltd.
- Auvik
- Aviatrix
- Axonius
- BackBox
- Bandura
- Beyond SSL
- Brocade
- Casque SNR
- Centrify
- Chronicle
- Cigent
- Citrix
- Claroty
- Cloudi-Fi
- Cloudify
- CloudMosa
- Corsa
- cPacket Networks
- CSPi
- CTModule
- Cubro
- Culinda
- Cyber Observer
- CyberArk
- Cybereason
- Cyberhaven
- CyberMDX
- Cybersixgill
- CyberX
- CyGlass
- Cylus
- Cynerio
- Cyr3con
- Cyturus
- D3 Security
- Darktrace
- DefendEdge
- Dell Technologies
- Delve
- Devo
- DFLabs
- Digital Defence
- Digital Realty
- DisruptOps
- DivvyCloud
- Dragos
- EclecticIQ
- ElevenPaths
- empow
- Endace
- Enea
- Entrust Datacard
- Equinix
- Ericom
- Ericsson
- ESET
- Everbridge, Inc.
- Extreme Networks, Inc.
- FileOrbis
- FireMon
- Firesec
- Flowmon Networks
- ForeScout Technologies
- Fornetix
- FRIXTEL
- Garland Technology
- Geoverse
- Gigamon
- Glasswall
- Gradient Cyber
- Graylog
- HashiCorp
- Hughes Network Systems
- HYAS
- HyTrust
- ID Quantique
- Idaptive
- Image Analyzer
- ImmuniWeb
- Indeni
- Industrial Defender
- Infoblox
- Infocyte
- InSync Information Technologies
- Intel
- IntelliSite
- Intentionet
- Intezer
- Intsights
- IP Infusion
- Jamf
- Keyfactor
- Keysight Technologies
- Kiana
- Lenovo
- Lightspeed Systems
- LinkShadow
- LiveAction
- Lookout
- Lumu
- Malware Patrol
- McAfee
- Medigate
- Megaport
- Menlo Security
- METTCARE
- Micro Focus
- Mimecast
- MistNet
- NEC
- NetDialog
- Network Perception
- Nexusguard
- Niagara Networks
- NodeWeaver
- Alcatel-Lucent
- NoviFlow
- NowSecure
- Nozomi Networks
- Nucleon
- Nutanix
- NVIDIA
- NXP
- Okta
- OMICRON
- Open Cloud Factory
- OPSWAT
- Ordr
- OTORIO
- Owl
- PacketFabric
- PC Matic
- PenguinIN
- Pensando Systems
- Persistent Systems
- Picus
- Pluribus Networks
- PowerDMARC
- Pulse Secure
- Pureport
- Qualys, Inc.
- Quantum Xchange
- RAD
- Radiflow
- RangeForce
- Rapid7
- Red Hat
- RedSeal
- Refactr
- Restorepoint
- Ribbon Communications
- RingCentral
- Rubrik
- SAASPASS
- Saasyan
- Safe-T
- Safetica Technologies
- SCADAfence
- Seclore
- Seclytics
- SecurityBridge
- Sensilla
- SentinelOne
- Siemens
- Siemplify
- Skybox
- SmartHive
- Sonpo
- Spirent
- Splunk, Inc.
- StratoZen
- Sumo Logic
- Swimlane
- Syncurity
- SYSCOM
- Tanium
- TDI Technologies
- Telco Systems
- TelcoBridges
- TeleBright
- Tenable
- Teridion
- Thales
- ThreatConnect
- ThreatQuotient
- Tigera
- TG8
- TokenEx
- TrapX Security
- Trend Micro
- TriagingX
- Trinity Cyber
- TrueFort
- Tufin
- UBiqube
- Varonis
- Vectra
- Venafi
- Vijilan
- VoIP.ms
- Volon
- Votiro
- Wandera
- Wavespot
- Welotec
- Westermo
- WhiteHat
- Wind River (An Intel Company)
- Wire X Systems
- WitFoo
- WootCloud
- Xona
- Zadara
- Zenlayer
- Zentera
- Zero Nines
- Ziften
DevOps:
- Alibaba Cloud
- Amazon Web Services (AWS)
- Google Cloud
- HashiCorp
- Microsoft
- Oracle
- Red Hat
- Refactr
- VMware
Fabric Connectors:
- Alibaba Cloud
- Amazon Web Services (AWS)
- Cisco
- Google Cloud
- GreyNoise
- Guardicore
- Hewlett Packard Enterprise
- IBM Security
- Microsoft
- Nuage Networks
- Oracle
- ServiceNow
- Symantec
- VMware
Fabric-Ready Partners:
- 1touch.io
- ABB
- Acalvio
- ADVA Optical Networking
- Advantech
- Aislelabs
- Alcide
- Algosec
- Alibaba Cloud
- Altran
- AWS
- Amdocs
- Ampere
- Anomali
- AppNeta
- AppViewX
- Aptilo Networks
- Area 1
- Arista Networks
- Arm
- Armis
- Array Networks
- Asavie
- Asimily
- ATAR Labs
- Attivo Networks
- AudioCodes Ltd.
- Auvik
- Aviatrix
- Axonius
- BackBox
- Baffin Bay Networks
- Bambenek Labs
- Bandura
- Beyond SSL
- Brocade
- Casque SNR
- Centrify
- Chronicle
- Cigent
- Cisco
- Citrix
- Claroty
- Cloudi-Fi
- Cloudify
- CloudMosa
- Corsa
- cPacket Networks
- CSPi
- CTModule
- Cubro
- Culinda
- Cyber Observer
- CyberArk
- Cybereason
- Cyberhaven
- CyberMDX
- Cybersixgill
- CyberX
- CyGlass
- Cylus
- Cynerio
- Cyr3con
- Cyturus
- D3 Security
- Darktrace
- DefendEdge
- Dell Technologies
- Delve
- Devo
- DFLabs
- Digital Defence
- Digital Realty
- DisruptOps
- DivvyCloud
- Dragos
- EclecticIQ
- ElevenPaths
- empow
- Endace
- Enea
- Entrust Datacard
- Equinix
- Ericom
- Ericsson
- ESET
- Everbridge, Inc.
- Extreme Networks, Inc.
- FileOrbis
- FireMon
- Firesec
- Flowmon Networks
- ForeScout Technologies
- Fornetix
- FRIXTEL
- Garland Technology
- Geoverse
- Gigamon
- Glasswall
- Google Cloud
- Gradient Cyber
- Graylog
- GreyNoise
- Guardicore
- HashiCorp
- Hewlett Packard Enterprise
- Hughes Network Systems
- HYAS
- HyTrust
- IBM Security
- ID Quantique
- Idaptive
- Image Analyzer
- ImmuniWeb
- Indeni
- Industrial Defender
- Infoblox
- Infocyte
- InSync Information Technologies
- Intel
- IntelliSite
- Intentionet
- Intezer
- Intsights
- IP Infusion
- Jamf
- Keyfactor
- Keysight Technologies
- Kiana
- Lenovo
- Lightspeed Systems
- LinkShadow
- LiveAction
- Lookout
- Lumu
- Malware Patrol
- McAfee
- Medigate
- Megaport
- Menlo Security
- METTCARE
- Micro Focus
- Microsoft
- Mimecast
- MistNet
- NEC
- NetDialog
- Network Perception
- Nexusguard
- Niagara Networks
- NodeWeaver
- Alcatel-Lucent
- NoviFlow
- NowSecure
- Nozomi Networks
- Nuage Networks
- Nucleon
- Nutanix
- NVIDIA
- NXP
- Okta
- OMICRON
- Open Cloud Factory
- OPSWAT
- Oracle
- Ordr
- OTORIO
- Owl
- PacketFabric
- PC Matic
- PenguinIN
- Pensando Systems
- Persistent Systems
- Picus
- Pluribus Networks
- PowerDMARC
- Pulse Secure
- Pureport
- Qualys, Inc.
- Quantum Xchange
- RAD
- Radiflow
- RangeForce
- Rapid7
- Red Hat
- RedSeal
- Refactr
- Restorepoint
- Ribbon Communications
- RingCentral
- Rubrik
- SAASPASS
- Saasyan
- Safe-T
- Safetica Technologies
- SCADAfence
- Seclore
- Seclytics
- SecurityBridge
- Sensilla
- SentinelOne
- ServiceNow
- Siemens
- Siemplify
- Skybox
- SmartHive
- Sonpo
- Spirent
- Splunk, Inc.
- StratoZen
- Sumo Logic
- Swimlane
- Symantec
- SYSCOM
- Tanium
- TDI Technologies
- Telco Systems
- TelcoBridges
- TeleBright
- Tenable
- Teridion
- Thales
- ThreatConnect
- ThreatQuotient
- Tigera
- TG8
- TokenEx
- TrapX Security
- Trend Micro
- TriagingX
- Trinity Cyber
- TrueFort
- Tufin
- UBiqube
- Varonis
- Vectra
- Venafi
- Vijilan
- VMware
- VoIP.ms
- Volon
- Votiro
- Wandera
- Wavespot
- Welotec
- Westermo
- WhiteHat
- Wind River (An Intel Company)
- Wire X Systems
- WitFoo
- WootCloud
- Xona
- Zadara
- Zenlayer
- Zentera
- Zero Nines
- Ziften